Analyze Windows failed login events with a custom log view
Use NetCrunch to monitor and display failed logon activity on all Windows machines in your network by monitoring Windows Event Log.
NetCrunch Event Log view allows you to create views of the type of events that you would like to analyze. In this way, you can filter and display only selected events. In this example, we will look at the events related to Windows Failed Logons entries*.
- In NetCrunch Event Log go to History tab.
-
To edit the view, click on the cogwheel icon.
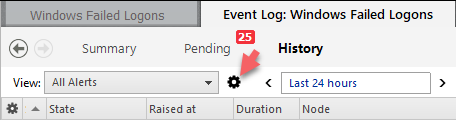
-
Click < Add Condition > and in the Expression field, select
Event IDis equal to4625.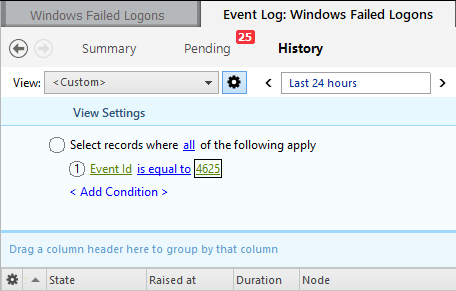
-
Click the Apply button. Now only events matching this filter will appear in the new Event Log view.
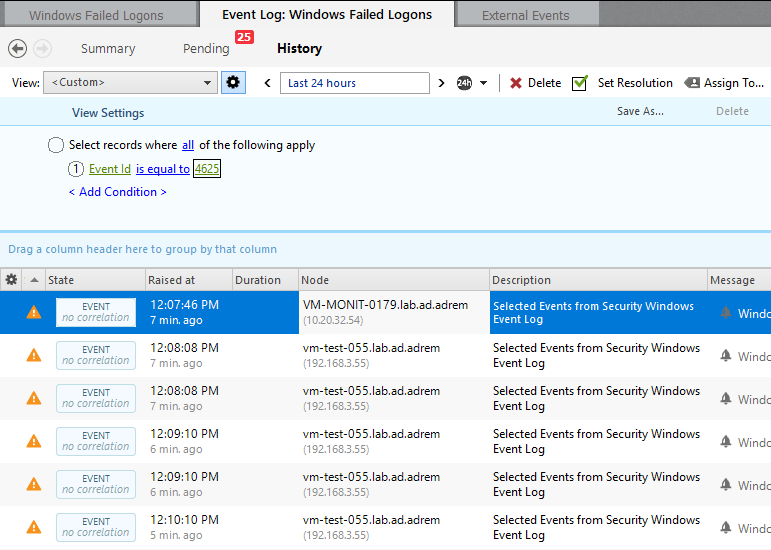
-
To keep the view of Windows Failed Logons entries for the future analysis, click Save As.., type Name of the view, e.g. Windows Failed Logons and Save.
-
Now you don't have to type proper filter expression each time when you want to see failed logons entries. Just expand the drop-down menu and choose the created view. Also, use another helpful option to set the date range or resolution.
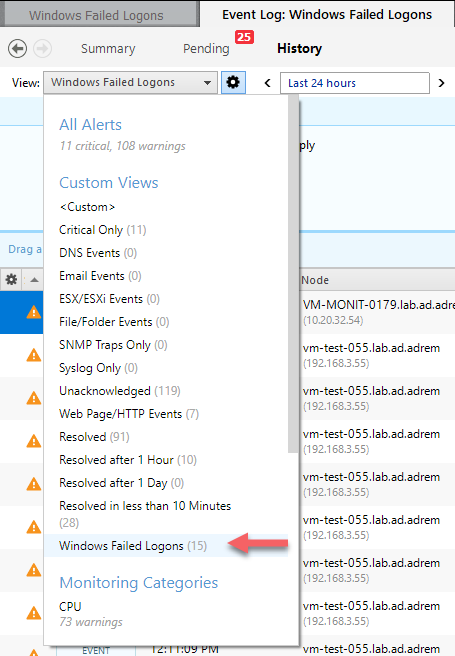
-
If you want to know, how to track Windows Event Log entries please refer to Microsoft Support Article - Description of security events in Windows 7 and in Windows Server 2008 R2.
- [28.05.2018]Monitoring Windows Event Logs for Warnings and Errors.
Learn how to monitor Windows Event Log to receive alerts and notifications when event with specified id appears.
- [12.02.2018]Process Monitoring with NetCrunch WMI Sensors.
Learn how to configure a node-specific WMI Object sensor to monitor a specific Windows process and generate an event when the process is restarted. This sensor-based monitoring strategy leverages the uniqueness of PID, against the generic name of a process.
- [24.05.2016] Correct Monitoring of Windows Processes on multi-core machines
This article will explain how NetCrunch monitors Windows processes and why these values are wrong in perfmon.