Advanced SSL Certificate monitoring
Nowadays secure connections are common, sites/servers without certificates are flagged as 'unsafe' and people tend to avoid such places on the web. This article will demonstrate how you can easily monitor not only if certificates are about to expire or expired but several other properties included in it.
SSL Certificate sensor
Pre-Requisites
This sensor (as all of the sensors in NetCrunch) can be added directly to the node. To start monitoring - node, where the certificate is located, needs to be added to the NetCrunch atlas.
For the purpose of this article - apache.adremsoft.com node will be used.
Sensor Capabilities
The sensor can check any SSL/TLS connection. It can check the SSL certificate expiration date and other certificate properties. Additionally, this sensor can check any certificate field.
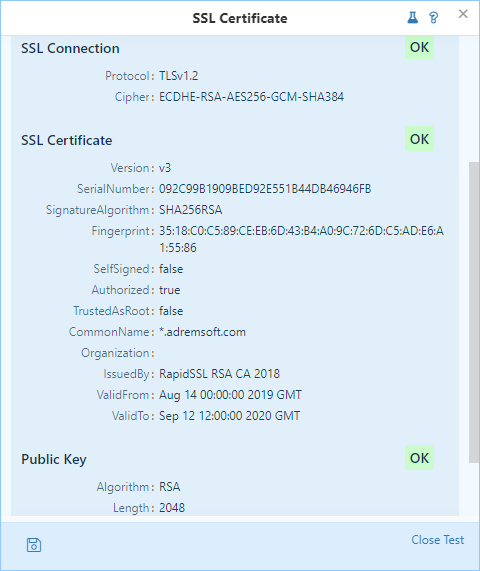
If the test is run against any certificate - it's possible to view all fields and properties of the certificate. If any of these fields is invalid - NetCrunch will display a warning.
Default Alerts
Most of the sensors in NetCrunch come with pre-configured alerts that are added by default. SSL Certificate is no exception - it contains multiple alerts that are added even before the sensor is saved.
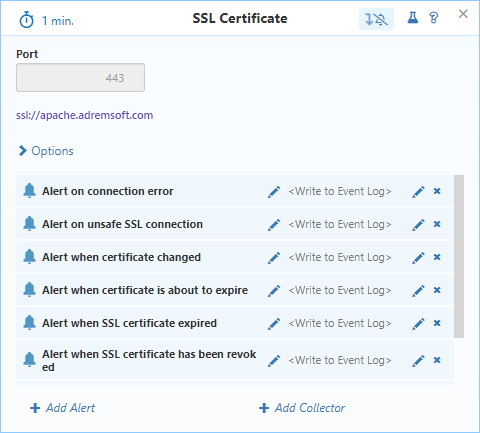
Default alerts will cover most of the cases in terms of basic monitoring - expiration, revoking, certificate changes, unsafe connections, a weak public key, and invalid CA.
Additional alerts in the sensor
Alerts above aren't only ones that can be configured. For individual cases, it's possible to monitor a lot more detailed information in the certificate - for example cipher used in a cert.
To add such alert:
- Click on +Add alert button
- Select
New Event on SSL Connection property conformance - Click on a
+icon - make sure that cipher is selected from the drop-down menu - Create an expression that will check if the proper cipher is used
- Select a name for the alert and save everything.
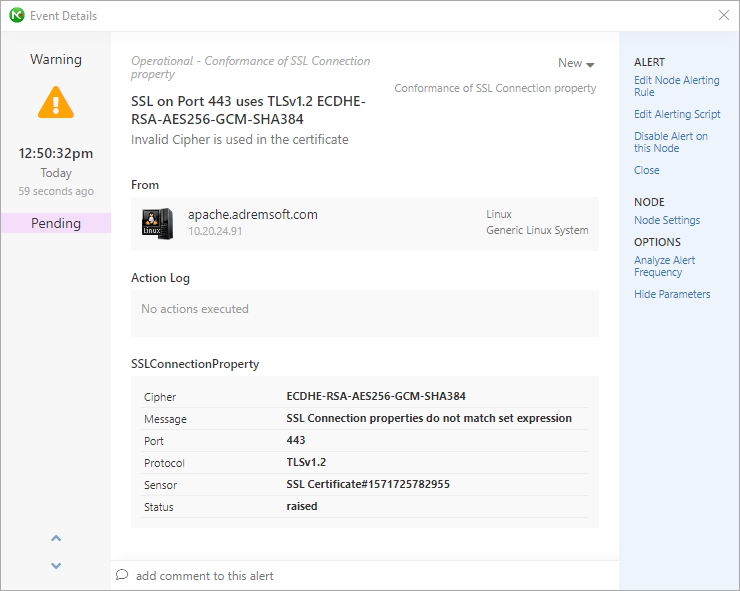
The moment that NetCrunch discovers that cipher isn't what it should be - an alert will be raised - with all important information in it.
Sensor template
If only one certificate is used - it's easy to keep track of the expiration date. If you need to track more than one certificate - things are getting harder to remember.
If all certificates should be monitored in exactly the same way (configuration of the sensor), it's best to use templating - it makes managing and configuring the monitoring setting much easier.
Template Creation
To create a template - click on + icon in the top right corner of the NetCrunch console and select 'Node Monitoring Template'
NetCrunch will ask for a name for the newly created Template.
If there is a node that is configured the way it should be configured on all nodes that will be using a template - use option Create from existing node
Template Configuration
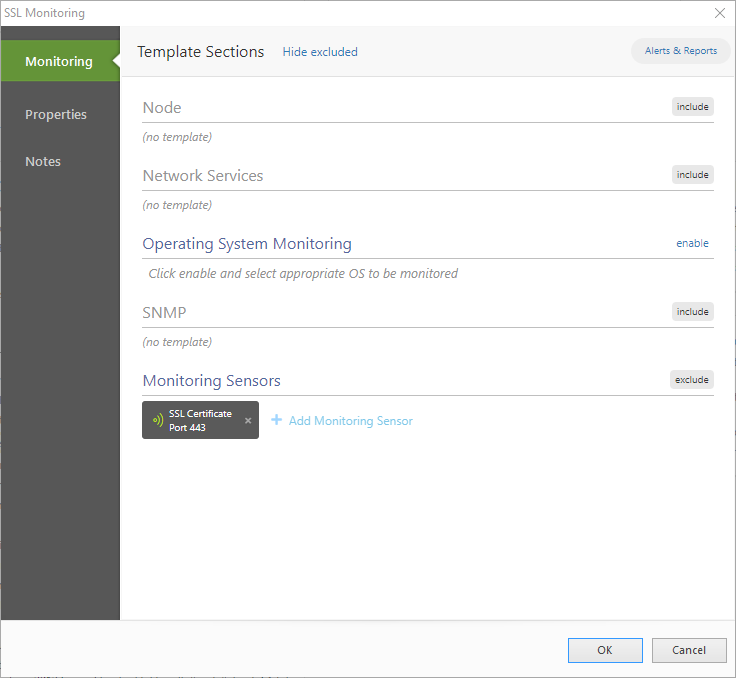
Configuration of the template looks exactly the same as the configuration of any node, For the purpose of this article, all segments apart of Monitoring Sensors will be excluded (they will not take configuration from the template)
- Exclude all sections (Node, Network Services, SNMP)
- Include Monitoring Sensors
- Add monitoring sensor - select the SSL certificate
- Select the reference node (Node against which the configuration will be tested - it's the best is to select the node where SSL cert is present)
- Add/Remove alerts
- Save everything
- Select a node (or a group of the nodes) where a template should be used
- Open Node settings and click on icon in top right corner
- Pick your template and save
Now all nodes will take sensor configuration from the node template. If anything needs to be changed globally - simply change it in the template - all nodes will inherit changes instantly.
- [20.07.2020] Setting up secure access to the monitoring server via Windows IIS Reverse Proxy with SSL certificate
A reverse proxy protects applications against cybercriminals and malicious software. It also allows limiting access to applications based on username, IP, domain, or geographical location.
- [02.07.2020] How to set up secure remote access to monitoring server using a NginX Reverse Proxy with SSL certificate
A reverse proxy protects applications against cybercriminals and malicious software. It also allows limiting access to applications based on username, IP, domain, or geographical location.
- [18.06.2020]How to monitor failed login attempts in Linux
One of the things administrators often do is check multiple failed login attempts in Linux. Monitoring them allows you to assess whether illegal or unwanted attempts to our network have occurred. In this article, we will show you how to track it automatically using NetCrunch.
- [05.02.2020]Monitoring Backup files
Backups are a vital part of any network infrastructure- they can contain personal data files, configurations or any important data. NetCrunch can help you track if backups are successfully created and if files are present in the designated directory
- [21.02.2019] Monitoring of Windows Updates and Pending Reboots
Updates are essential to keep network infrastructure safe and solid, NetCrunch 10.5 provides new functionality that allows monitoring of update status, missing updates, and failed installations. It can also notify when the system is running for too long without installing updates. This article shows how to check which updates are available and how to set these two essential sensors.
- [12.09.2018]Monitoring SSL Certificate expiration date with NetCrunch
Learn how easy you can monitor an SSL certificate with NetCrunch. Use it to be informed about SSL certificate expiration time and the properties of such certificate.
- [10.05.2018]How to use NetCrunch data parsers with REST sensor
See how easy it is to use REST sensor in NetCrunch to get any data, and process it with parsers for counters and statuses. It can be added to any view as a widget for live visibility.
- [12.04.2018]Generate NetCrunch SSL certificate with Microsoft Certificate Authority server
Learn how to use certificates generated by Microsoft Certificate Authority to secure Web Access connection to the NetCrunch server.