Monitoring Windows Event Logs for Warnings and Errors.
Learn how to monitor Windows Event Log to receive alerts and notifications when event with specified id appears.
Monitoring Windows Event Log entries by category
All Windows events are classified and grouped by category, for example, Application, System, Security, etc. You can see them in Windows Event Viewer.
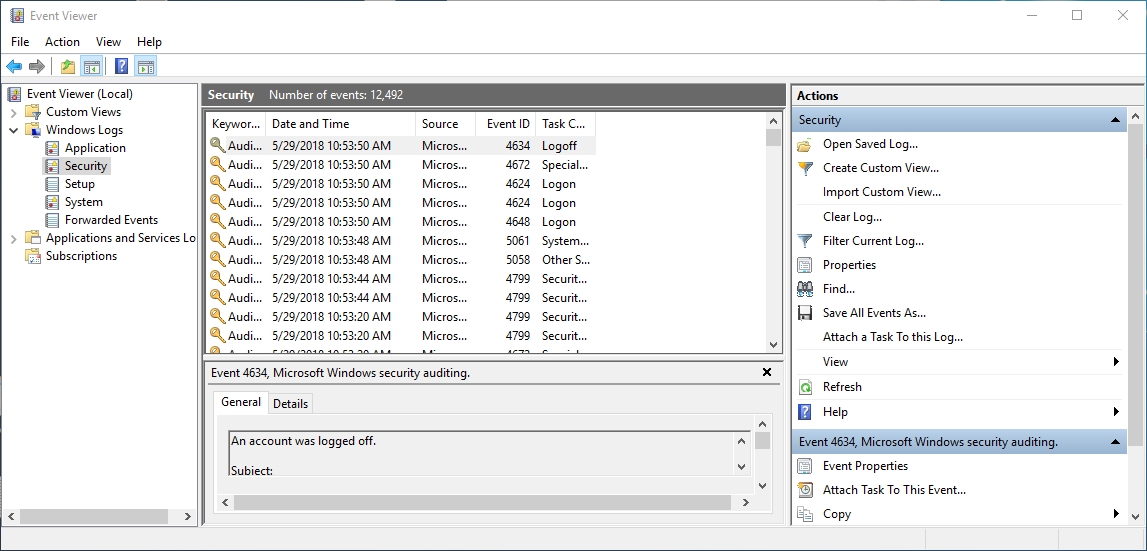
For this example, we will use the Security Log:
- Go to MonitoringMonitoring Packs & Policies and create New Monitoring Pack.
- Select the Alerting & Data Collection tab and use Add Alert button.
- Choose the Windows category and double-click on New Event for Received Windows Event Log Entry.
- In Alerting Rule window in Windows Event Log file field, select Security.
-
In the Expression field, select
Event TypeequalError. Add conditionEvent TypeequalWarningand change all toanyin the condition clause to include any of these types of entries.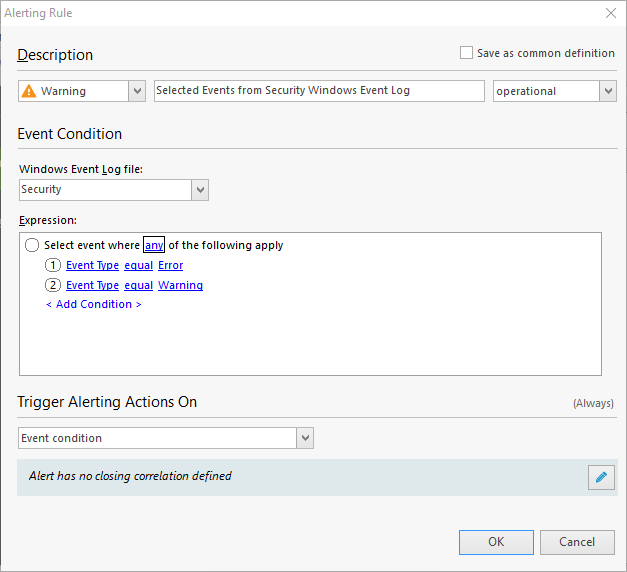
-
(Optional) You can change the detection severity of the event if default Warning does not fit your needs. This setting will dictate the use of appropriate Alert Escalation Script.
-
Assign nodes to this Monitoring Pack and save Monitoring Pack settings.
By default, when any Warning or Error event occurs on assigned Windows machines, NetCrunch will generate the alert (or status change) and write the notification to the NetCrunch View Event Log.
Defining how NetCrunch should react to occurring event
How NetCrunch reacts to detection can be customized by first creating or modifying an Alert Escalation Script and then assigning it to a particular Alert.
- Go to Monitoring Alert Escalation Scripts and use the Add Alerting Script button.
- Set script name (or leave a default one) and Add Action to Run Immediately.
- Choose Notify user or group action.
- In action parameters, choose the profile you want to send notifications to which.
- Save Alerting Script settings.
- Go to MonitoringMonitoring Packs & Policies and choose early created monitoring pack.
- In Alerting & Data Collection tab, right-click on alert, hover on Assign Predefined Alerting Script and choose previously defined alerting script.
- Save Monitoring Packs settings.
- Alert Escalation Scripts can be unique and customized per alert, which allows NetCrunch to react uniquely to a broad range of detections.
-
*Manage Notification profile configuration using ToolsUser & Access Rights Manager: select user and add a notification profile. Provide the user's email address and choose the desired message format. You can also specify Time Restrictions when NetCrunch can send notifications.
Monitoring Windows Event Logs for a single event
In this scenario, an alerting rule is created to detect a failed credential validation event or failed the user-password challenge. This rule can be specified by EventID, rather than by category, and uses a threshold to eliminate needless alerts.
- Go to MonitoringMonitoring Packs & Policies and create New Monitoring Pack.
- Switch to Alerting & Data Collection tab and use Add Alert button.
- Select Windows tab and double-click on New Event for Received Windows Event Log Entry.
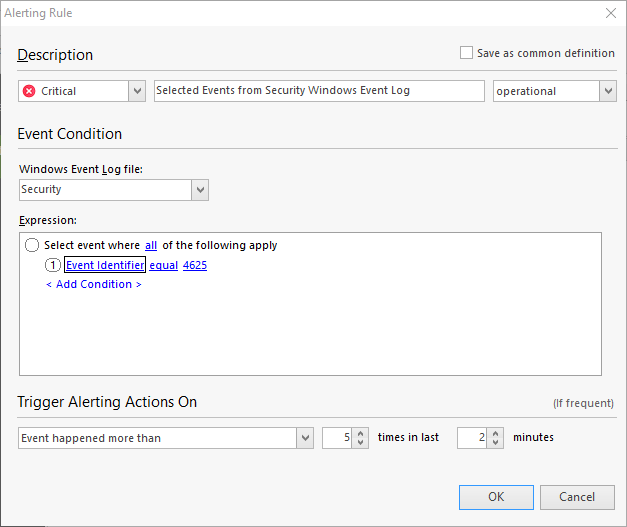
- In Alerting Rule window in Windows Event Log file field select Security.
- In the Expression field, select
Event Identifierandequal, type4625. -
In the section Trigger Alerting Actions On select Event happened more than and chose e.g.,5 times in last 2 minutes.
-
(Optional) You can change the severity of this event, too, e.g., Critical.
- Assign nodes to this Monitoring Pack and save Monitoring Pack settings.
You can also assign a unique alerting script with actions.
Read more about Windows security events in the following articles:
- [06.07.2018]Analyze Windows failed login events with a custom log view
Use NetCrunch to monitor and display failed logon activity on all Windows machines in your network by monitoring Windows Event Log.
- [12.02.2018]Process Monitoring with NetCrunch WMI Sensors.
Learn how to configure a node-specific WMI Object sensor to monitor a specific Windows process and generate an event when the process is restarted. This sensor-based monitoring strategy leverages the uniqueness of PID, against the generic name of a process.
- [24.05.2016] Correct Monitoring of Windows Processes on multi-core machines
This article will explain how NetCrunch monitors Windows processes and why these values are wrong in perfmon.