7 proactive ways of monitoring your network in order to stay compliant with GDPR
The General Data Protection Regulation (GDPR) is about to come in-effect on May 25th, 2018 in the European Union. In a nutshell, it’s the first law of its kind which will define what is third-party personal data and how this data should be protected. Moreover, the law stipulates hefty fines on individuals and businesses alike, in case personal data is leaked into the wrong hands and the IT administrator (or business owner) does not handle the situation accordingly.
We would like to think that the mishandling of personal data should not happen. However, it’s impossible to account for human error, or for the simple malice of malware developers trying to snoop around for personal information.
So, aside from arming your network with barriers to entry, what can you do proactively, in order to stay compliant with the GDPR?
Monitor your system logs for unusual logins.
The Windows Event Log, SSH log, and other system logs contain a wealth of information which can be useful in diagnosing and detecting a potential threat. Multiple concurrent logins from the same account, for example, can be a sign of password sharing inside your business. Multiple failed logins, on the other hand, are usually a sign of a brute-force attack.
In fact, any unusual logins to your production servers should be a cause for concern. This includes logins during non-standard hours.
Log monitoring is a daunting task if done manually. However, with a log parser, this task can be automated and become hassle-free. You can set NetCrunch to parse a log of your choice and notify you of any event which might be a cause of a concern.
Read more: Postifix Log Monitoring, Monitoring Windows Events
Set NetCrunch to check up on your antivirus logs.
As malware becomes more advanced, having a proper antivirus protection is the key. However, some malware programs are able to quietly disable the antivirus software from performing a scheduled scan or updating the virus definition file. When unnoticed, this can lead to the virus quietly spreading across the network, all while fishing for your personal data.
With that in mind, set NetCrunch to monitor your antivirus logs – both for events that should happen and for events that didn’t happen. For example, a daily scan should generate a “scan completed” entry in the log file. Is the entry missing? If so, you can be immediately notified.
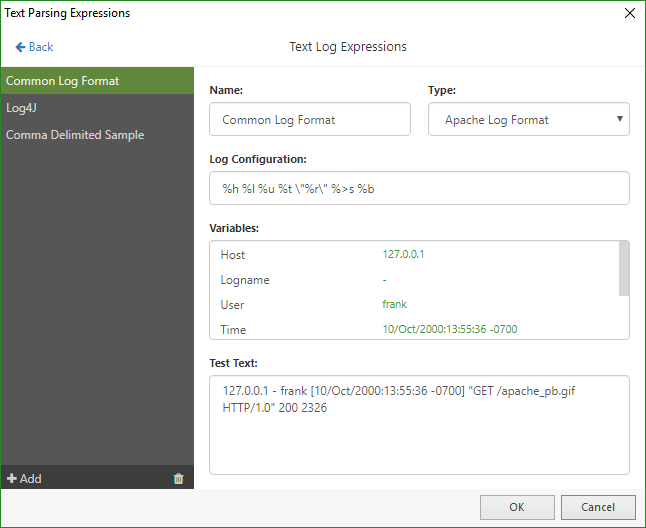
Read more: Monitoring Text Files in NetCrunch
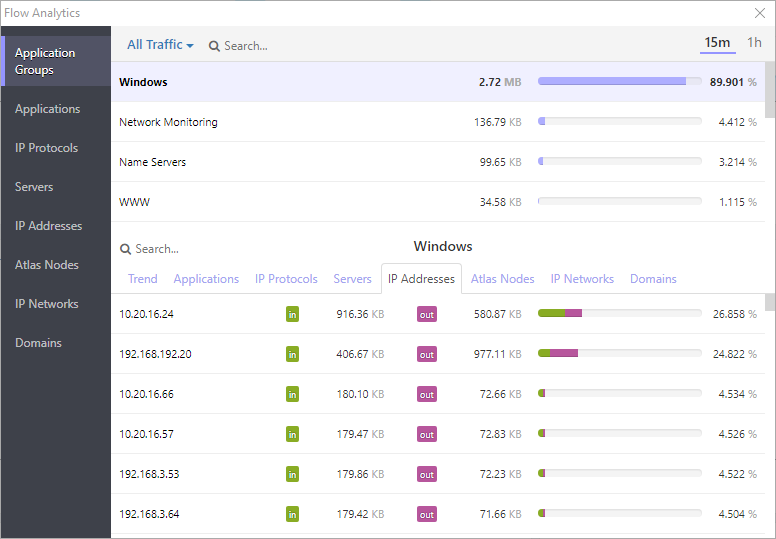
Monitor your bandwidth and usage across your network.
Very often having a per-node view is not very useful. While working on a computer or a server, you may know which ports are used and which services the current node is hosting or utilizing. However, with a multitude of nodes and IoT devices, it’s difficult to see what’s exactly going on in your network. Especially in the age of Bring Your Own Device (BYOD), knowing what’s running in your network is becoming ever more trivial. With proper network monitoring software, you can have an overview of every protocol, port, and connection within your network. Early detection of unusual services running on your network can make the difference between knowing where your sensitive data is traveling and having something unintentionally exposed to the internet – for example, through a user-installed file-sharing service.
Read more: Traffic analytics
Monitor for events that didn’t happen.
In similarity to the point #2 above, a key preventative measure in network security is early detection of anomalies, whether big or small. Were your backups done? Are all critical Windows updates installed properly? In numerous cases, software solutions might fail before they are capable of producing a log output. Monitoring for events which should have happened, but did not, will quickly allow you to hone in on misbehaving software or hardware. Moreover, in the age of critical SMB1 or OpenSSH vulnerabilities being discovered daily, keeping your production servers patched should be a top priority.
Monitor your sensitive files or folders.
This especially includes monitoring the time of changes. Are your files accessed in non-standard hours? If so, this might be a good time to review who has the access to these files, and what is the reason behind accessing them at non-business hours.
Read more: Monitoring Files and Folders
Monitor your website and its content.
There are numerous tools out there that will check up, or most likely PING, your website to let you know if it’s still online. While these tools are definitely an excellent starting point in website monitoring, a simple PING is not sufficient at ensuring that your website is secure. After all, modern websites include logins and forms, shopping carts and other integrations which the end-user utilizes.
With GDPR in place, as the administrator or business owner, you are responsible for making sure that any personal information entered into any parts of your website indeed stay personal. Given the numerous phishing attacks and vulnerabilities with server software being discovered nearly on daily basis, it is difficult to be certain that all aspects of your website have never been quietly compromised.
This is why monitoring your website and its scripts in production servers are critical. NetCrunch can handle this for you, by monitoring your website and its contents, and immediately alerting you when something changes without your authorization. The sooner you know about a foreign script being injected, the sooner you are able to fix the issue and alert the proper authorities in compliance with GDPR regulations.
Read more: Monitoring Web Pages, Apache Web Server Monitoring
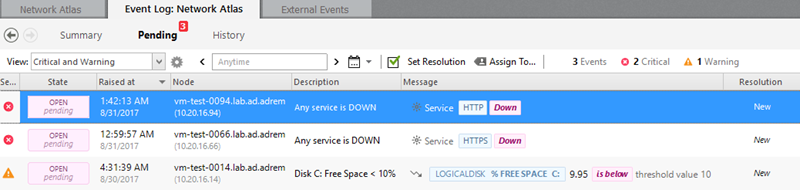
Use Pending Alerts view to analyze and record changes in your network
One of the key responsibilities of the administrator is keeping records of what happened on the network during the breach, and presenting these records to the proper authorities. You will need to assess what happened, provide documentation on how it happened, and provide information on who might be affected by the mishandling of personal data.
While network monitoring software can indeed be overwhelming with the number of alerts, NetCrunch handles the alerts differently. The Event Correlation feature allows NetCrunch to automatically close alerts which do not need your attention (for example, a service being down and then coming back up). In essence, you will only need to check up on Pending Alerts. Pending Alerts are the only ones which still need your attention – for example, antivirus logs showing a scan which is not completed, Windows Update logs showing a failed upgrade or a backup failing. Get into a habit of checking your Pending Alerts view, and keep a record of it. At best, you’ll never have to worry about anything misfiring. But when a personal data breach does happen, you’ll have a clear picture of your entire network and everything that happened. This will allow you to quickly make the proper documentation for the authorities, as well as identify who could be affected by the breach.